Indexing & Abstracting
Full Text
Review ArticleDOI Number : 10.36811/rjcse.2021.110003Article Views : 1Article Downloads : 1
Implementation of Local Area Network (LAN) & Build a Secure LAN System for BAEC Head Quarter
Osman Goni1* and Md. Abu Shameem2
1Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka-1207, Bangladesh
2Principal Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka- 1207, Bangladesh
*Corresponding Author: Osman Goni, Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka-1207, Bangladesh
Article Information
Aritcle Type: Review Article
Citation: Osman Goni, Abu Shameem. 2021. Implementation of Local Area Network (LAN) & Build a Secure LAN System for BAEC Head Quarter. Res J Comput Sci Eng. 2: 01-15.
Copyright: This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Copyright © 2021; Osman Goni
Publication history:
Received date: 03 April, 2021Accepted date: 15 May, 2021
Published date: 05 June, 2021
Abstract
Network security is the process of taking physical and software preventative measures to protect the underlying networking infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure, thereby creating a secure platform for computers, users, and programs to perform their permitted critical functions within a secure environment. A local area network (LAN) is a computer network within a small geographical area such as a home, school, computer laboratory, office building or group of buildings. A LAN is composed of inter-connected workstations and personal computers which are each capable of accessing and sharing data and devices, such as printers, scanners and data storage devices, anywhere on the LAN. LANs are characterized by higher communication and data transfer rates and the lack of any need for leased communication lines. A data network is an interconnected system of computers, peripherals and software over which data files and messages are sent and received. LAN is only one type of computer network. LAN define is Data com system allowing a number of independent devices to communicate directly with each other, within a moderately sized geographic area over a physical communications channel of moderate data rates. Fiber-optic communication is a method of transmitting information from one place to another by sending pulses of infrared light through an optical fiber. The light is a form of carrier wave that is modulated to carry information. Fiber is preferred over electrical cabling when high bandwidth, long distance, or immunity to electromagnetic interference is required. This type of communication can transmit voice, video, and telemetry through local area networks or across long distances. Optical fiber is used by many telecommunications companies to transmit telephone signals, Internet communication, and cable television signals. Researchers at Bell Labs have reached a record bandwidth distance product of over 100 petabit × kilometers per second using fiber optic communication. Communication between remote parties can be achieved through a process called Networking, involving the connection of computers, media and networking devices. When we talk about networks, we need to keep in mind three concepts, distributed processing, network criteria and network structure. The purpose of this Network is to design a Local Area Network (LAN) for a BAEC (Bangladesh Atomic Energy Commission) Head Quarter and implement security measures to protect network resources and system services. To do so, we will deal with the physical and logical design of a LAN. The goal of this Network is to examine of the Local Area Network set up for a BAEC HQ and build a secure LAN system.
Keywords: LAN, Secure LAN, BTCL, UTP, RJ-45, Bandwidth, Wavelength, ISP, Firewall, BAEC
Introduction
A local area network (LAN) is a collection of devices connected together in one physical location, such as a building, office, or home [1]. A LAN can be small or large, ranging from a home network with one user to an enterprise network with thousands of users and devices in an office or school. A local area network (LAN) is a group of computers and associated devices that share a common communications line or wireless link [2]. Usually, the server has applications and data storage that are shared in common by multiple computer users. A local area network may serve as few as two or three users (for example, in a home network) [3]. Networks are divided into two main categories: Local Area Networks (LANs) and Wide Area Networks (WANs). These two types of networks have different characteristics and different functionalities. In general, a LAN is a collection of computers and peripheral devices in a limited area such as a building or campus [4]. A LAN is usually under the domain of a single organization such as an institutional or department. The internet is, however, more than just a physical connection of LANs, internetworking protocols and standards are also needed. Network’s models serve to organize, unity, and control the hardware and software components of communication and networking. The Internet has revolutionized many aspects of our daily lives [5]. It has affected the way we do business as well as the way we spend our leisure time. Count the ways you have use the internet recently. Perhaps you have sent electronic mail (email) to a business associate, paid a utility bill, read a newspaper from a distant city, or looked up a local movie schedule all by using the internet or maybe you researched a medical topic, booked a hotel reservation, chatted with a fellow trekker or comparison shopped for a car. The internet is a communication system that has brought a wealth of information to our fingertips and organized it for out use [6-8]. The internet is a structured, organized system. Bangladesh Atomic Energy Commission is a scientific research organization and regulatory body of Bangladesh. Its main objective is to promote use of atomic energy for peaceful purposes. It was established on 27 February 1973. So, it is important to Design, Deployment and Implementation of Local Area Network (LAN) at BAEC Head Quarter.
Bangladesh Atomic Energy Commission
Bangladesh Atomic Energy Commission (BAEC) was established in 1973 as a multidisciplinary R&D organization with the view of promoting peaceful uses of nuclear energy in Bangladesh. From the very beginning of its formation, BAEC started R&D works in areas covering physical science, bioscience, engineering and nuclear medicine for human welfare and economic uplift of the country. At present, the BAEC has grown as the largest organization for scientific and technological research in Bangladesh.
Bangladesh Tele Communication Company Limited
BTCL or Bangladesh Telecommunications Company Limited is the largest telecommunications company in Bangladesh. The company was founded as the Bangladesh Telegraph & Telephone Board (BTTB) following Bangladesh's independence in 1971. On July 1, 2008 the BTTB became a public limited company and was renamed as BTCL. BTCL provides land-line telephone services in Bangladesh's urban areas, including domestic long-distance calling and international services as well as internet services. In 2004, the Bangladesh Government issued a number of PSTN licenses to private companies, but they were barred from providing services in the lucrative Dhaka market (which accounts for the majority of the nationwide market). The monopoly held by BTCL was broken when other operators started to receive licenses from 2007 [9].
Optical Fiber Network
Fiber optic internet cable is increasingly popular. This is due to the higher speeds and bandwidth it can provide compared to standard Ethernet or Wi-Fi signals delivered via coaxial or even copper wire from street-level exchanges. This means that fiber networking is a far better choice where high speeds are advantageous or for particularly intensive data transfer needs. Fiber optic bandwidth is usually significantly higher than a typical Ethernet connection. Fiber is also safe to use in high-voltage locations, and in areas where flammable gases or other harsh chemicals or weather conditions are likely to be a factor. This can be another important factor in choosing fiber optic cables for broadband delivery and telecoms as opposed to standard Ethernet.
Local Area Networks
Local area networks, generally called LANs, are privately-owned networks within a single building or campus of up to a few kilometers in size. They are widely used to connect personal computers and workstations in company offices and factories to share resources (e.g., printers) and exchange information. The Local Area Network (LAN) is one of the most important types of information networks in providing communication within a limited community such as universities and institutions. The LAN consists of an interconnected group of computers and other communication devices, which are connected to each other through an integrated engineering system. They are distributed within relatively small geographical areas and characterized by high speed and lack of errors in communication. Thus, the local area networks are a mixture of interrelated devices, equipment and institutions, where they form a fabric called networks, these networks mainly rely on essential physical components and software to operate efficiently. The present analytical study seeks to understand both the basic components of the operation of local networks and to recognize and define the role of each of the means of communication adopted within the local network in order to construct and operate the LAN.
Research Background
Networks A network is a set of devices (often referred to as nodes) connected by communication links. A node can be a computer, printer, or any other device capable of sending and/or receiving data generated by other nodes on the network.
Optical Fiber Cable
A fiber-optic cable, also known as an optical-fiber cable, is an assembly similar to an electrical cable, but containing one or more optical fibers that are used to carry light. The optical fiber elements are typically individually coated with plastic layers and contained in a protective tube suitable for the environment where the cable is used. Different types of cable[1] are used for different applications, for example, long distance telecommunication, or providing a high-speed data connection between different parts of a building.
Unshielded Twisted Pair (UTP) Cable
Cable is the medium through which information usually moves from one network device to another. Unshielded twisted pair (UTP) is the most popular and is generally the best option for Local Area networks (See figure 1).
Figure 1: Unshielded twisted pair.
The quality of UTP may vary from telephone-grade wire to extremely high-speed cable. The cable has four pairs of wires inside the jacket. Each pair is twisted with a different number of twists per inch to help eliminate interference from adjacent pairs and other electrical devices. The tighter the twisting, the higher the supported transmission rate and the greater the cost per foot. The EIA/TIA (Electronic Industry Association/Telecommunication Industry Association) has established standards of UTP and rated six categories of wire (additional categories are emerging) [10].
|
Table1: UTP Cable additional categories. |
||
|
Category |
Speed |
Use |
|
1 |
1 Mbps |
Voice Only (Telephone Wire) |
|
2 |
4 Mbps |
Local Talk & Telephone (Rarely used) |
|
3 |
16 Mbps |
10BaseT Ethernet |
|
4 |
20 Mbps |
Token Ring (Rarely used) |
|
5 |
100 Mbps (2 pair) |
100BaseT Ethernet |
|
1000 Mbps (4 pair) |
Gigabit Ethernet |
|
|
5e |
1,000 Mbps |
Gigabit Ethernet |
|
6 |
10,000 Mbps |
Gigabit Ethernet |
RJ45 Connector
Most standard Ethernet data cables have a core consisting of four twisted-pair wire strands, making eight individual wires in total. Male RJ45 plugs separate and correctly terminate these eight individual wires. In other words, RJ45 wiring is based on an 8P8C (8 position, 8 contact) configuration. Standard RJ45 is defined as a mechanically-keyed variant on a generic 8P8C body. Mechanically keyed essentially means that RJ45 connectors also include an additional tab. This extra tab is designed to prevent them from being mated with any other socket standards which are visually similar, but electrically incompatible. It also prevents accidental disconnection.
Bandwidth and Window of Fiber Optic Cable
In May 2002, the ITU-T organization divided the fiber optical communication system into six bands as O, E, S, C, L and U6. Multi-mode optical fiber at 850nm is known as the first window, single-mode optical fiber at O band is referred to as the second band. C band is called as the third window, L band is the fourth window and E band is the fifth window. The following table shows the wavelength bands for both multimode fiber optic cable and single-mode fiber optic cable [11].
|
Table 2: Fiber Optic Wavelength. |
|||
|
Frequency band |
Window |
Wavelength range (nm) |
Frequency range (THz) |
|
/ |
1 |
850(770-910) |
/ |
|
Original band |
2 |
1260-1360 |
237.9-220.4 |
|
Extended band |
5 |
1360-1460 |
220.4-205.3 |
|
Short wavelength band |
/ |
1460-1530 |
205.3-195.9 |
|
Conventional band |
3 |
1530-1565 |
195.9-191.6 |
|
Longer wavelength band |
4 |
1565-1625 |
191.6-184.5 |
|
Ultralength wavelength band |
/ |
1625-1675 |
184.5-179.0 |
The frequency range in the table above refers to the frequency of light. According to the formula, speed = wavelength x frequency, we can easily figure out the frequency of light. Its relation to the transmission loss of fiber optic cable and wavelength has been displayed as follow:
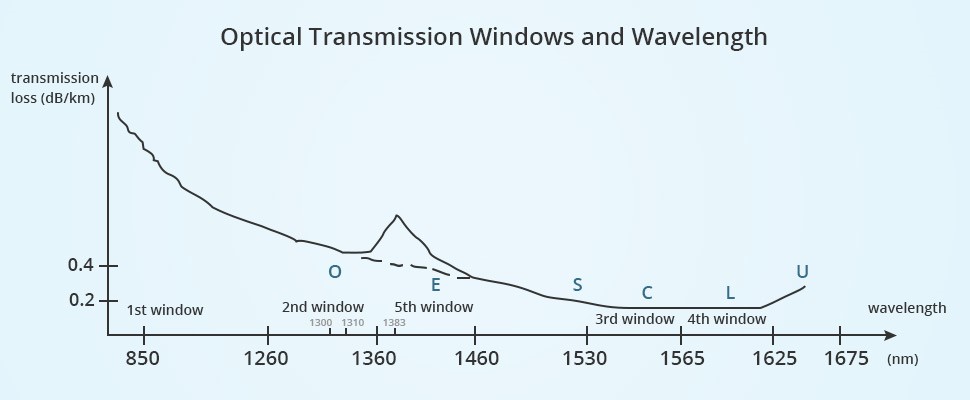
Figure 2: Optical Transmission Windows and wavelength.
In the early days of fiber optic communication, the LED was employed as a light source due to its low price. Multi-mode fiber optic cables that operate at 850nm and 1300nm became the first choice for building small network, while single-mode optical fiber cables, working at 1310nm and 1550nm with laser as the light source were the foundation for constructing large network. If there were more windows available for single-mode optic cable, one fiber optic cable would achieve ultra-high-speed transmission by transmitting signals at different wavelength at the same time by employing WDM (wavelength division multiplexing) technology, thus maximizing the potential of single mode fiber. Telephone and network and be using at the same time via ADSL (asymmetric digital subscriber line) modem. That’s because voice and data use different frequency. And this principle is similar with WDM and ADSL technology, which are usually applied in main networks that require higher bandwidth [12].
Optical Fiber Cable at OSI Model
The interface between an optical fiber and a twisted pair Cable can be at different layers of the OSI model. At the Physical layer a media converter can be used. It will transform the electrical Ethernet signal to Ethernet over fiber. At the data link layer, a layer 2 (Ethernet) switch can be used with copper and fiber interfaces. At the network layer a router can be used with an optical (fiber) interface and a copper (RJ45) interface. Conversion at the physical layer is a signal conversion. At the data link layer Ethernet packets will be switched or retransmitted at a different interface. At the network layer routing of IP packets to a different interface will take place.
Internet
The Internet is a worldwide telecommunications system that provides connectivity for millions of other, smaller networks; therefore, the Internet is often referred to as a network of networks. It allows computer users to communicate with each other across distance and computer platforms.
Internet Service Provider
An Internet service provider (ISP) is an organization that provides a myriad of services for accessing, using, or participating in the Internet. Internet service providers can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned.
Network Security
Network Security Essential Network security has become more important to personal computer users, organizations, and the military. With the advent of the internet, security became a major concern and the history of security allows a better understanding of the emergence of security technology. The internet structure itself allowed for many security threats to occur. The architecture of the internet, when modified can reduce the possible attacks that can be sent across the network. Knowing the attack methods, allows for the appropriate security to emerge. Many businesses secure themselves from the internet by means of firewalls and encryption mechanisms. The businesses create an “intranet” to remain connected to the internet but secured from possible threats. The entire field of network security is vast and in an evolutionary stage. The range of study encompasses a brief history dating back to internet’s beginnings and the current development in network security. In order to understand the research being performed today, background knowledge of the internet, its vulnerabilities, attack methods through the internet, and security technology is important and therefore they are reviewed [13]. When developing a secure network, the following need to be considered: 1. Access- Authorized users are provided the means to communicate to and from a particular network 2. Confidentiality- Information in the network remains private 3. Authentication - Ensure the users of the network are who they say they are 4. Integrity - Ensure the message has not been modified in transit 5. Non?repudiation - Ensure the user does not refute that he used the network [14].
Security Services
It is a processing or communication service that is provided by a system to give a specific kind of production to system resources. Security services implement security policies and are implemented by security mechanisms. Security Services are Confidentiality, Authentication, Peer Entity Authentication, Data Origin Authentication, Integrity, Connection Oriented Integrity [15].
Basic Technologies of Computer Network Security
The basic technologies of computer network securities are Firewall technology, Data encryption technology, Intrusion detection technology, Anti-virus technology [16].
Types of Attacks
4 Types of Attacks 1) Interception: Watches packets 2) Interruption: Steals or disturbs the data 3) Modification: Changes the data 4) Fabrication: Sends another message apart from original but having the same sender’s name [17].
Security Protocols
a) Secure Socket Layer
It is used in secure exchange of information between web browser and web server. It gives 2 security services. 1. Authentication 2. Confidentiality It has five layers:
|
Application Layer |
|
Secure Socket Layer |
|
Transport Layer |
|
Internet Layer |
|
Data Link Layer |
|
Physical Layer |
Transport Layer uses HMAC
SSL have 3 sub protocols. Handshake protocol- Connection Establishment. Record protocol -Actual message protocol. Alert Protocol - If client/ server detects error other party discloses the connection and the secret key is deleted.
Computer Network Information Security Policy
Set up a firewall
Firewalls are an important means to ensure network security, network management applications through the use of technology, packet filtering technology and agent technology, effectively control network access permissions, comprehensive data to external restrictions and discrimination [18].
Access control
Security policy and security model based on access control body set access permissions, such as to the identity of the user, password authentication, in order to gain the true identity of the user, to facilitate tracing network behavior [18].
Strengthening Intrusion Detection
Network intrusion detection is a real-time network detection system can effectively compensate for the lack of firewalls and other protective means [19].
Information encrypted
Information technology is the key encryption technology to achieve information security, help strengthen security, through a particular encryption algorithm translated the important plaintext cipher text, so unauthorized users can not directly read the raw data, even if the data file is lost or stolen, as long as difficult to crack the key, so it will not lead to the leakage of confidential information, which greatly ensure information security [18].
Close some not commonly used services and ports
From the theory in terms of computer security, computer systems were more port system is also more secure. For using the computer in the process, especially when the operating system is installed in inadvertently will not have to install some service functions and ports, it will not only occupy a certain system information and also reduce the security of computer systems sex. In addition, in order to understand the use of the user interface can be installed port monitoring program. It can be determined by examining those ports are not commonly used. In addition, once a virus into a computer system, the monitoring program can automatically alarm, some of the function can automatically shut down the port, effectively prevent hacker intrusion [18].
IP addresses are correct hidden PC
IP address of the hacker and virus attacks must have a condition that is on the network and information attacks must have a real IP address to be a hacker to obtain the user's IP address mainly through the use of network technology to detect host information view, some of the traditional hackers and virus attacks, Flop overflow attacks and so must obtain address as preconditions. Therefore, the user should use a computer system when hiding your IP address, using a proxy server is the most common way to hide IP address, a hacker can only detect the proxy server IP address, but cannot get the user's real IP address You cannot find the real IP address will not be able to attack, effective maintenance of computer information and network security [18].
Authentication technology
Authentication should include at least verification protocol and license agreement. A variety of network applications and computer systems are needed to confirm the legality through authentication, and then determine its personal data and specific permissions. For authentication system, the legitimate user's identity is easy to be someone else pretending to be its most important technical indicators [18].
Timely installation of Vulnerability Patch
Vulnerability can be utilized during the attack weaknesses can be software, hardware, procedural shortcomings, functional design or improper configuration. University of Wisconsin Miller gives a research report on today's popular operating systems and applications, noting that the software cannot be without flaws and loopholes [18].
File encryption and digital signature technology
File encryption and digital signature technology is to improve the security and confidentiality of information systems and data, one of the secrets to prevent external data theft, interception or destruction primary technologies. Depending on the role, file encryption and digital signature technology is mainly divided into data transmission, data storage, data integrity of the three kinds of discrimination [18].
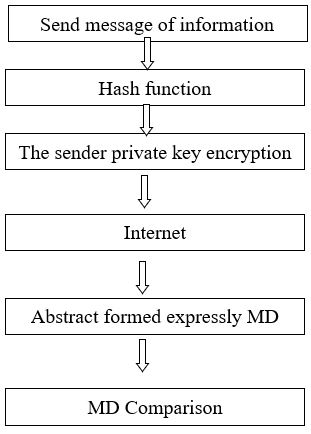
Figure 3: Usually, the digital signing process MD means Encryption key.
Data integrity identification technology is mainly involved in the transmission of information, access, processing of data related to the identity and to verify the contents, to confidentiality requirements, including general identification passwords, keys, identity, data items of the system by Comparative validation object input feature value meets the preset parameters, to achieve data security [18].
Security Services and Processes
Security is fundamentally about protecting assets. Security is a path, not a destination. As we analyze our infrastructure and applications, we identify potential threats and understand that each threat presents a degree of risk. Security is about risk management and implementing effective countermeasures. Security services and processes depends on: Authentication, Authorization, Auditing, Confidentiality, Integrity [19].
Security in Linux Networks
The Linux operating system is built with security features, as it provides the file access permission mechanism, which prevents the unauthorized users in gaining access to the files [20].
Firewalls
A firewall is one of the most widely used solutions for the Internet world. All traffic inside to outside and vice versa, must pass through the firewall. Different types of firewalls have different types of rules and security policies. The authorized traffic will be sent based only on local policies. The firewall itself is protected, i.e.; it uses a trusted hardware and operating system [21].
Methodology
“Methodology” implies more than simply the methods intend to use to collect data. It is often necessary to include a consideration of the concepts and theories which underlie the methods.
More over methodology guides the researcher to involve and to be active in my particular field of enquiry. Right from selecting the topic and carrying out the whole research work till recommendations; research methodology drives the researcher and keeps him on the right track. The entire research plan is based on the concept of right methodology [22].
In my research paper, the methodology is following:
Implementation
Design, planning & deployment of LAN at BAEC Head Quarter
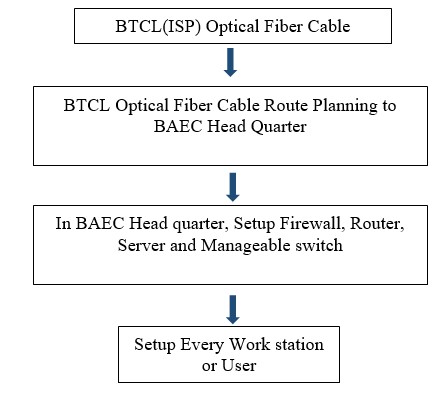
Fiber optical Communication is a method of transmitting information from one place to another by sending pulses of light through an optical fiber [23]. The light forms an electromagnetic carrier wave that is modulated to carry information.
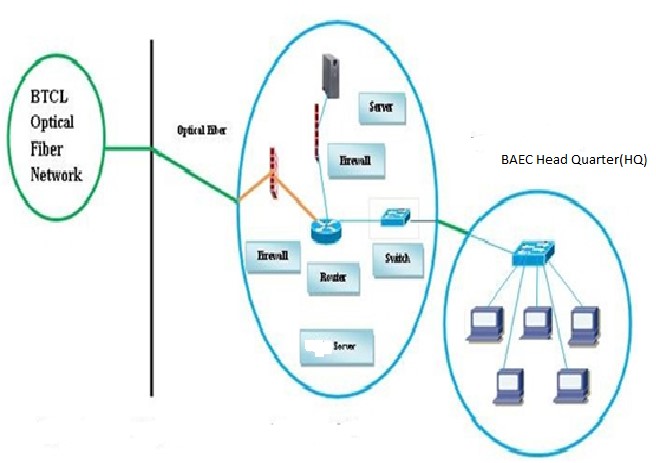
Figure 4: Optical fiber connection From BTCL to BAEC Head Quartet.
This day’s most organizations build their own LAN infrastructure with special consideration of security measures to protect their resources from any kind of attacks [24]. Building a well-secured LAN requires designing of network topology before deciding which physical devices to be purchased or technologies to deploy [25]. A topology design is defined as the identification of networks and their interconnection points, the size and the scope of the network, and the type of interconnecting devices used [26]. Every network requires a structured planning and designing before deployment it that requires internet access [27], Internet connectivity factors should be included into the plan, Includes a practical design of network internet connectivity backbone [28]. Procedures of selecting equipment’s are added and planning designs their networks. The LAN of BAEC head quarter interconnects more than 90 computers using various network media. The previous LAN was not properly working; as a result, the internet service was interrupted. Hence, the previous LAN was redesigned and up gradated using a Proxy server of Dell T320, Router: Cisco 2901, and other network media. Currently, internet service is smoothly running at BAECHQ.
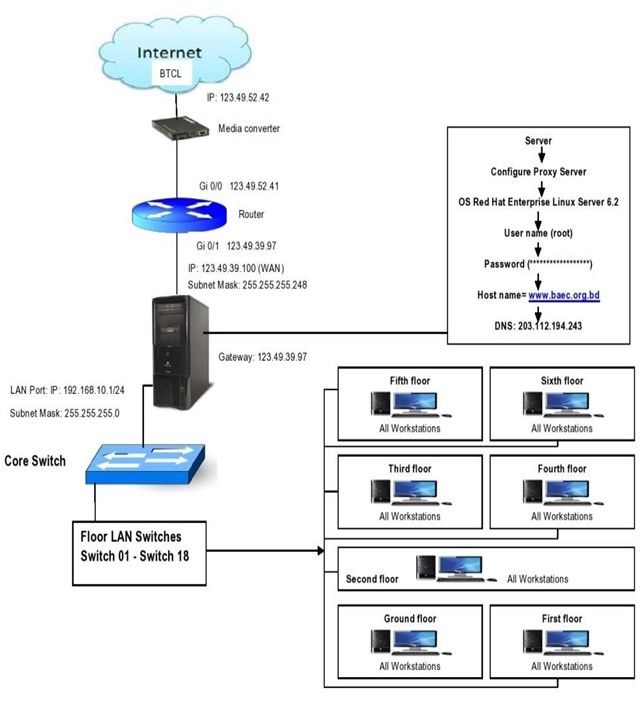
Figure 5: LAN Connection of BAEC Head Quarter.
Hardware Selection
LAN Related Device Selection
Router Model 2901; we are using Cisco router. It is reliable and trusted to IT Community. Bandwidth is a factor for router as well and 2900 series router required MBPSA Duplex operations easily choose a Cisco router supports upgrade IOS version will enable to enjoy some good facilities. Switch Model 2960; we also use Cisco manageable switch for their backbone. It is tested and performs well for IT backbone. Cable & Connector; Choosing good brand cable. Now days Cat-6 cables are most popular [29]. It will be best for LAN wearing (it has really good sailed protection). The RJ 45 and is 8 - Position modular connector that looks like a large phone plug [30]. Servers; Server Selection is important for each server services. Many reputed ISP in Bangladesh runs with brand servers. Need to choose a brand which spare parts are available local support for the brand is essential.
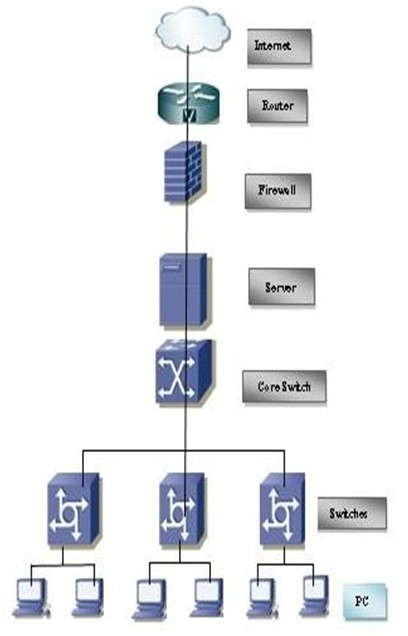
Figure 6: Local Area Network (LAN) Diagram at BAEC Head Quarter.
Configuration
Configuring Router
We install the routers hardware properly before configuring and commissioning. We install all hardware properly to avoid damage. We Read all supplied manual properly before installing router. We Take a PC/Laptop with terminal emulator software (Hyper Terminal for windows minicom for Linux). The PC should have at least a standard communication port (Com-1) connect Router’s console to Pc’s communication port using console cable. We Turn on Pc’s and router power switch. Terminal will display router’s booting information. We have successfully booted router and configure using setup facility the router is now configured properly with initial configuration and ready touse.
Configure Server
Proxy Server satisfies web browser’s query by sending requested web page. Proxy does two main operations. First operation is to reduce internet bandwidth charges. And the second option is to limit web access to authorized user/PC. Users configure their web browser’s to use the proxy server instead of going to the internet directly [31]. When a user sends any web request, proxy takes the request. Proxy is the only service, which heavily uses CPU, memory and storage simultaneously. We Installing Operating System and then configuration following:
Operating System
Buying operating system (OS) in Bangladesh is really a big headache. There are very few commercial operating systems. All commercial operating systems supports are not also available locally. So, we need to depend on foreign support we choose OS Centos-6.5 which includes squid with its entire options precompiled [32]. Server OS should have a large amount of hardware support. Compare with your operating systems hardware compatibilities List (HCL), before choosing the OS. Installation Media; Install Linux operating system from any comfortable media like CD ROM, Hard disk including all network installation method. Installing OS; we have chosenCentos-6.5 Linux operating system. All other versions installation is almost same. We cover Centos-6.5 installation step bystep.
a) Disk Partition Setup.
b) Boot loader configures.
c) Firewall configure manual.
d) Set root Password.
e) Package group selection automatically.
f) Escape boot diskette creation.
g) Video card configurations.
h) Configuring monitor.
i) Installation complete then reboot the system.
Network configuration is Linux; we configure Linux server to enjoy networking features. Linux Networking Facility by default Linux support network, when will install a system, Networking facility will be installed. Moreover, is a stalled system without a NIC card Networking will be available with to interface. IO helps to run all Network related services when other NIC is not available we can check/control network by “Network” service script nicely (/etc/rc,d/init.d/network). Use the following command connected to start/stop network Service.
[root@ns1 root] # Service network stop. [root@ns1 root] # Service network start. [root@ns1 root] # Service network status. Determining IP address; now a day’s commonly all Pc’s come with a NIC, when Linux is installed this first device is called “eth0” second one is “eth1” and so on. We can determine the IP address of these interfaces using “ifconfig”
[root@snmp root] # if config.
Assigning IP address using “if config”. We can assign an IP address on “eth0” interface using the” if config” command. This is the most common method.
[root@snmp root] # if config eth0 10.0.0.100 net mask 255.255.255.0 up.
The “up” at the end of the command activates the interface after assigning the IP. But this procedure is not permanent. When you will reboot the system the IP setting will be lost. To make this IP permanent, you need to change the script file for the particular interface. All files will be found in “/etc/sysconfig /network-scripts” directory. Now restart the “network” service to take effect. We need to restart the network service each time makes any type of change into these files. [root@nsl root] # service network restart use “if config” command to see the change. It will show the new IP setting. [root@snmp root] # if config. Assigning IP address using “netconfig”, we can also do it automatically using some graphical utility. “netgonfig” is a beautiful utility that we can use to edit those files automatically. It will offer to fill up essential fields.
Result
Bangladesh Atomic Energy Commission (BAEC) is the largest scientific organization in Bangladesh. If we want to connect international network, we have to setup Local Area Network. For this in my paper, we have shown and practically configured Local Area Network at Bangladesh Atomic Energy Commission and build a secure LAN System. We smoothly installed Local Area Network (LAN) networking with secure system at BAEC HQ. As a result of this LAN network, Bangladesh Atomic Energy Commission Head Quarter is getting a high-speed internet service with security. Future work In Future, we extended our Local Area Network by adding Access Point (AP) and Wi-Fi devices. We add more network devices to service the end user who are working at BAEC Head Quarter. Conclusion This Research Paper proposed a secure design for network and system in Linux and windows environment using the latest technology. We should have an understanding with communication models, network service & architecture, media, devices and protocol suites. We are expected to have network service. Every network requires a regular maintenance such as storage maintenance, remote resource access, user management, log management and some other management. Monitoring is a regular task for all network system. It is mandatory when the system is dedicated to public service to make a user friendly and dependable monitoring system. After applying our proposed design, deployment and implemented highly reliable local area network mechanism. Therefore, all the mechanisms thoroughly discussed in this paper to work well together and provide strong Local Area Network (LAN) system at BAEC Head Quarter.
Biography
Osman Goni was born at Chandpur, Bangladesh in 25th September 1982. He has completed his Diploma-in-Computer Engineering and obtained 3rd place from Bangladesh Technical Education Board (BTEB) and B.Sc. in Computer Science & Engineering from the Department of Computer Science and Engineering of World University of Bangladesh (WUB) and M.Sc. in Computer Science & Engineering from the Department of Computer Science and Engineering of Jagannath University (JnU) in Bangladesh. Currently he is working as an Engineer (Assistant Engineer, Computer Science and Engineering) at the institute of Computer Science in Bangladesh Atomic Energy Commission. He is member of Institution of Diploma Engineers, Bangladesh (IDEB) and associate member The Institution of Engineers, Bangladesh (IEB) and associate member Bangladesh Computer Society (BCS). His research interests include Computer Hardware and Networking, artificial intelligence and Robotics, Cyber Security, E-Commerce etc.
Md. Abu Shameem was born in Bhairab, Kishoregonj, Bangladesh in 1969. He was completed Bachelor of Science in electronics & telecommunications engineering from the department of electronics & telecommunications engineering Prime University, Mirpur, Dhaka and Master of Science in telecommunications engineering from the department of electronics & communications engineering East West University, Dhaka. He worked as a senior instructor in department of youth development from January’1994 to December’ 1995. Currently he is working as a principal engineer & divisional head of computer system & networking division at the institute of computer science in Bangladesh atomic energy commission. His research interest includes communication engineering, networking & security system, server administration and instrumentation & control system etc.
References
1. Wijuntunga, Pradeepa. LOCAL AREA NETWORKS (LANS) AND THEIR APPLICATION IN LIBRARIES. [Online] The Central Library University of Colombo, Colombo 3, Sri Lanka. http://web.simmons.edu.
2. Baird, Patricia M, Borer, Beatrice. 1987. An Experiment in Computer Conferencing Using a Local Area Network. s.l.: Electronic Library.
3. Flower, Eric, Thulstrup, Lisa. Setting Up a Public Use Local Area Network. s.l.: Wilson Library Bulletin, 63: 45-47.
4. WIKIPEDIA. Local area network. 2007. https://en.wikipedia.org/wiki/Local_area_network.
5. Broadband, Asianet. Importance of Internet Technology for Easy Life. [Online] March 16, 2020. [Cited: March 16, 2020.] https://asianetbroadband.in/importance-of-internet-technology-for-easy-life.
6. Bakardjieva, Maria. The Internet in Everyday Life. 2009. [Cited: July 29, 2009.] https://people.ucalgary.ca.
7. Internet Society: The Internet in Everyday Life. University of Calgary, Canada: SAGE Publications Ltd, May 31, 2012.
8. Singh, Rakesh. 10 Ways Internet Changed our Lives Positively - Here all we Explained. [Online] July 7, 2018. [Cited: July 7, 2018.] https://www.pdevice.com.
9. WIKIPEDIA. [Online] https://en.wikipedia.org/wiki/BTCL.
10. Technology, Florida Center for Instructional. Cabling, Florida Department of Education. [Online] 1997-2013. https://fcit.usf.edu/network/chap4/chap4.htm.
11. Moris. 2012. The Bandwidth and Window of Fiber Optic Cable. https://community.fs.com/blog/the-bandwidth-and-window-of-fiber-optic-cable.html.
12. The Bandwidth and Window of Fiber Optic Cable. [Online] September 18, 2012. https://community.fs.com/blog/the-bandwidth-and-window-of-fiber-optic-cable.html.
13. Ajala Funmilola, Akanbi Oluwafemi. 2015. Review of Computer Network Security System. Network and Complex Systems. 40-46.
14. Network Security. Priyank Sanghavi, Kreena Mehta, Shikha Soni. 8, August 2013, International Journal of Scientific and Research Publications. 3: 1-5.
15. Significances and Issues of Network Security. Dr. B V Ramana Murthy, Prof. Vuppu Padmakar, Ms. A. Vasavi. 2014. International Journal of Advanced Research in Computer and Communication Engineering. 3: 6922-6929.
16. Analysis and research of computer network security. Shan, Jie. 7, 2014, Journal of Chemical and Pharmaceutical Research. 6: 874-877.
17. A Survey on Network Security. Sridevi, C. 5, 2017, Global Journal of Computer Science and Technology: Network, Web & Security. 17.
18. The Security and Protection Strategy Study of Computer Network Information. Junyan Shi, Juanjuan Li1. China: s.n., 2016. 2nd International Conference on Electronics, Network and Computer Engineering (ICENCE 2016).
19. DESIGN AND IMPLEMENTATION OF SYSTEM AND. Seifedine Kadry, Wassim Hassan. 2005 - 2008, Journal of Theoretical and Applied Information Technology.
20. Security Analysis in Open-Source Linux Network. Mukesh Kumar Mishra, Dinesh Goyal. 8, 2013, International Journal of Engineering Research & Technology (IJERT). 2.
21. Mukesh Kumar Mishra, Dinesh Goyal. 2013. International Journal of Engineering Research & Technology (IJERT). 2.
22. Foez Md Iqbal Hossain, Misbah uddin md Imran, Md. Saleh Ahmed. 2013. Hybrid Wireless Mesh Network. Dhaka: BRAC UNIVERSITY.
23. Hui, Rongqing. Introduction to Fiber-Optic Communications. Kansas: Academic Press, 2019.
24. Pollard, John. Network infrastructure security basics. [Online] https://help.returnpath.com.
25. Tutorial, DCN. DCN - Network LAN Technologies. [Online] https://www.tutorialspoint.com/data_communication_computer_network/network_lan_technologies.htm.
26. Information, In Depth Tutorials and. LAN Topologies (Networking). [Online] https://what-when-how.com/networking/lan-topologies-networking.
27. BIAN, WU XUE YI. 2015. Computer network planning and design of the second edition. s.l.: Machinery Industry Press.
28. John, Wolfgang. 2008. On Measurement and Analysis of Internet Backbone Traffic. Göteborg, Sweden: Chalmers Reproservice.
29. Tech, Sterlite. CAT6 UTP -Data Cable. [Online] 2017. https://www.stl.tech/optical-interconnect-products.
30. Kordz. RJ45 CAT6 Field Termination Connector & Strain Relief. [Online] 2019. https://static1.squarespace.com.
31. Hat, Red. Red Hat Satellite 5.8 Proxy Installation Guide. [Online] February 1, 2017. [Cited: February 1, 2017.] https://access.redhat.com/documentation.
32. Technology, ZeroNines. Z9_CentOS_Installation_Guide_AAv7_3.3_20141003.docx. [Online] October 3, 2014. [Cited: October 3, 2014.] https://zerodownsoftware.com.




















